As described on the first part, there’s a kwown non working scenario when using Azure MFA , ADFS and Alternate Login ID combined.
I’ve decided to share the regular expression that you could use in case there are multiple SMTP domains that you would like to include as an expection for MFA on your environment.
SCENARIO
Keep in mind that this is just a temporary solution, the goal should be to get all your users MFA Enabled.
In case you would like to have just one domain added as an exception not to request MFA. You can build a simple rule with an exception including the e-mail address attribute, in the condition add E-mail Address claim ends with @domain.com.
But there could be a challenge if you have multiple smtp domains to add as an exception. In ADFS Access Control Rules are inclusive (this means and condition), so is not possible to add multiple domains as an exception.
If that’s your case, you need to build a regular expression.
SOLUTION
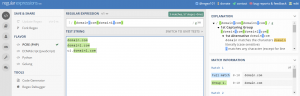
The advantage of using a regular expression, is that you can define multiple domains on a single exception. So let’s say you would like to add an exception for the domains @woodgrovebank.com and @tailspintoys.com, then you should add an exception with the following configuration:
Permit users and require multi-factor authentication
Except:
With E-mail claim
regex matches:
(?:@woodgrovebank.com|@tailspintoys.com) in the request
Tip: The following free tool is truly useful if you would like to validate your regular expression : regular expressions 101
Example of the regex I’ve created:
In order to add the E-mail address as part of the claim for the exception, you must perform the following steps under ADFS to add the E-mail address in the claim:
Into the ADFS Console, go to Claims Provider Trusts:
Right Click on Active Directory and select Edit Claim Rules…:
Click on the Add Rule… button :
In rule template select Send LDAP Attributes as Claims:
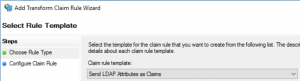
Leave the configuration as follows:
Attribute store: Active Directory
LDAP Attribute: E-Mail Addresses
Outgoing Claim Type: E-mail Address
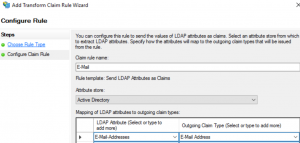
Keep in mind that this change may affect other Claim Rules that are using the E-mail address attribute.
Alternate solution:
If you have multiple SMTP domains to exclude, you can build a rule as the opposite to only require MFA if the SMTP address matches a specific domain:
In the conditions add:
and with E-mail Address claim ends with @your domain in the request
and require multi-factor authentication
I hope you find it helpful!