Hello
Introduction
This is my first post as I’ve decided to revamp my blog. I’ve been busy after my brief pass at Microsoft and my current job at a local partner.
This time I wanted to share with you a little trick I learned while troubleshooting a domain join in ADDS (Azure Active Directory Domain Services).
There are many reasons why you would need to join a machine to your ADDS domain, in this case was due to administrative purposes. It’s necessary to manage the Organizational Units and GPO’s.
Issue:
When trying to add a brand new virtual machine in Azure on the same vnet of the ADDS domain. You may encounter the following error message:
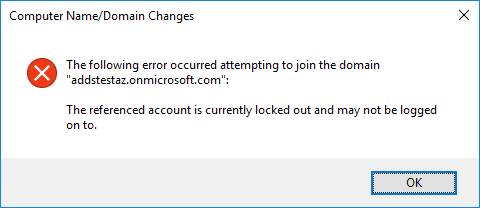
So the error message says “The referenced account is currently locked out and may not be logged on to”
Solution
First things first, confirm if the user account you are using to authenticate is not locked out. In my case I verified the account wasn’t locked.
After that double check if you enabled password hash synchronisation.
Here’s the procedure for Cloud-based Identities
Here’s the detail in case you are synchronizing the accounts from an AD instance
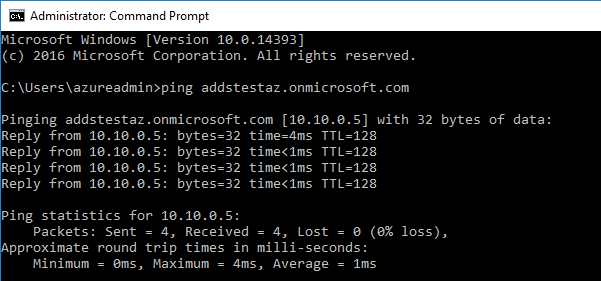
Check connectivity by a simple ping to your domain:
After that I’ve decided to check the EventLog on the machine and I found an Event ID # 4097 with error code 1909 as detailed on the image below:
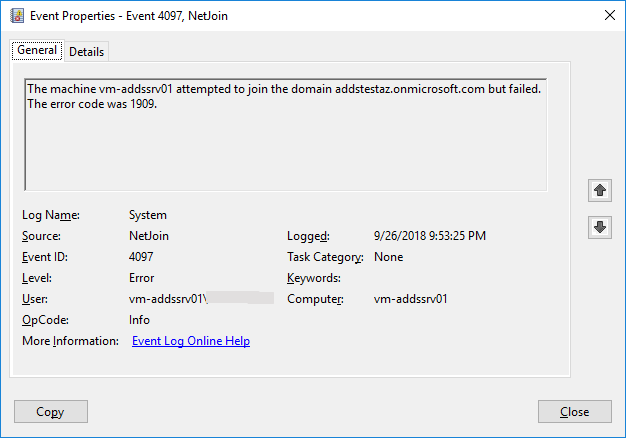
Checking at the Microsoft’s error code reference, indeed code 1909 is associated to a locked account:
ERROR_ACCOUNT_LOCKED_OUT
1909 (0x775)
The referenced account is currently locked out and may not be logged on to.
But in this case it is not quite exact, as I double checked if the user account used to provision the ADDS Domain in Azure was member of the group Azure AAD DC Administrators and it wasn’t.
Only members of this domain can join machines, so I’ve added the account as member of the group. In case you find yourself on the same situation follow the next steps:
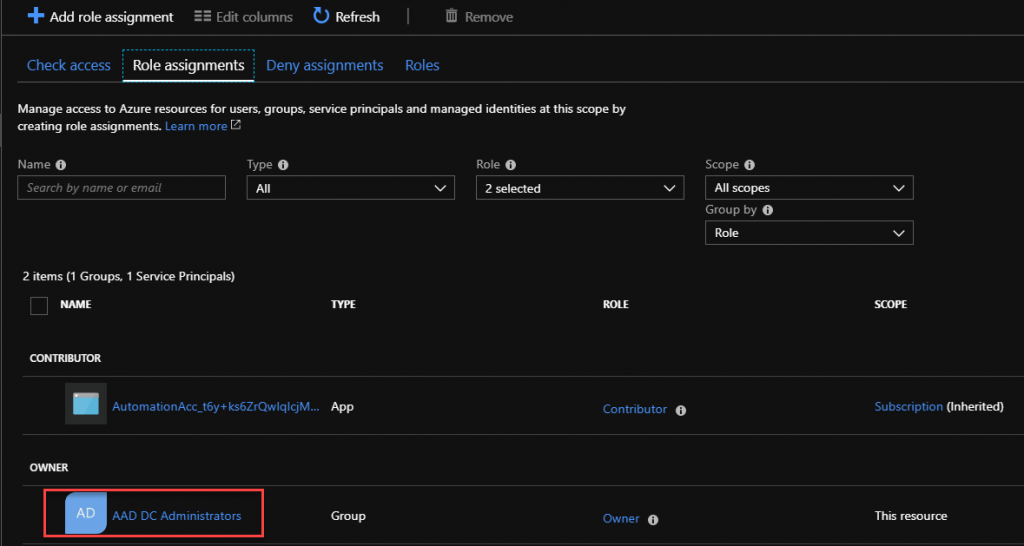
- Into the Azure portal go to your ADDS Domain, and click on Access control (IAM) on the left, and then on the Role asignments tab:
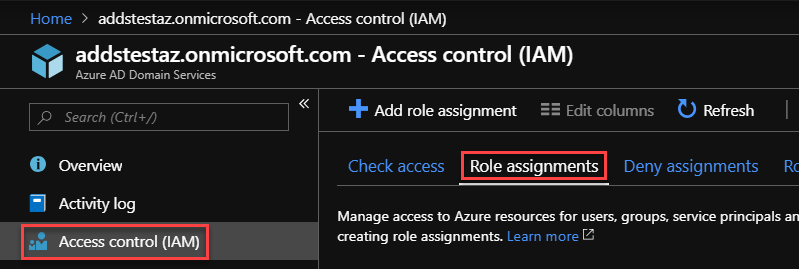
- At the Role assignments blade, click onto the AAD DC Administrators group under OWNER:
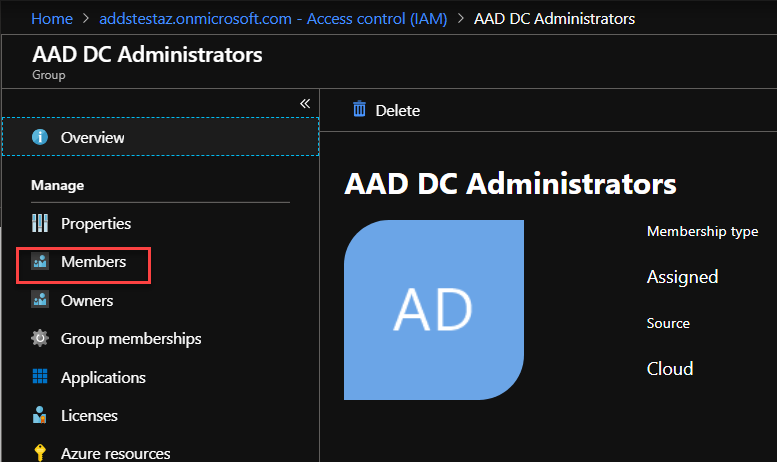
- After that, click on Members:
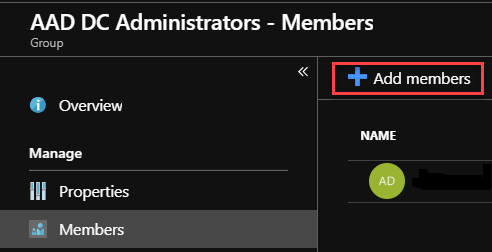
- Click on the Add members button:
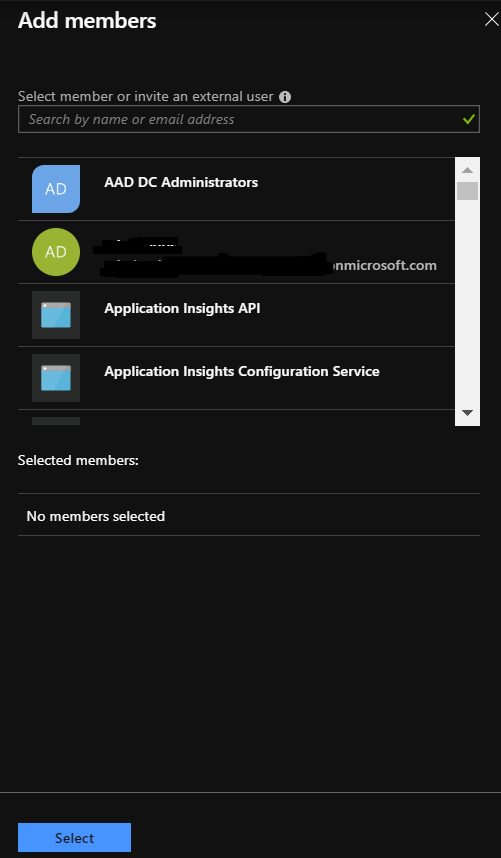
- Select the user account from the list and click on Select:
Now, retry to join the machine to the domain and provide your credentials:
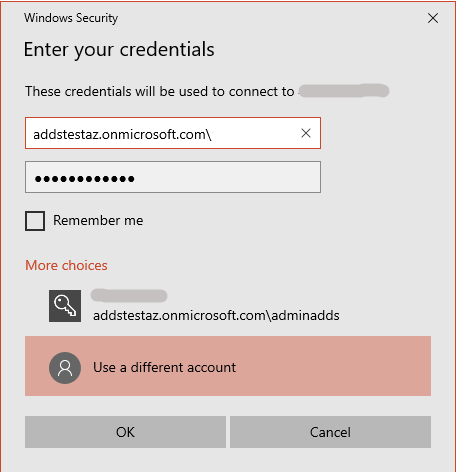
And voila!, now your machine has succesfully joined the domain:
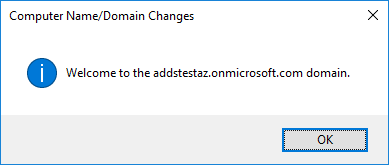
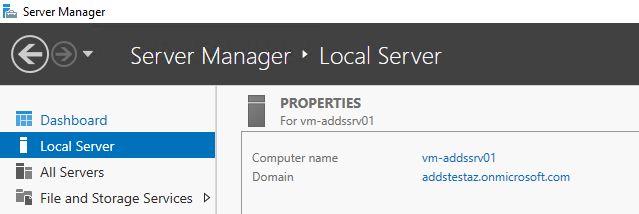
Conclusion
After that I managed to install the ADDS management tools into the server and Start managing the ADDS Domain:
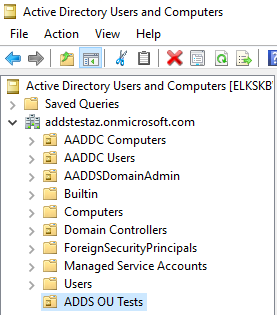
I hope you find it helpful.
Until next time!
